Email Authentication - SPF, DKIM, DMARC
Email authentication is a method of showing mail is from you and not spammers. Anybody can send mail that has your name and address on it, but when email authentication is properly set up it will be more likely to be marked as spam, or filtered out before it reaches the recipient. There are three main types of email authentication in use today, SPF, DKIM, and DMARC. Each provides an extra layer of authentication to your emails, and makes it harder for scammers to pretend to be you.
Caution: Incorrect settings cause your domain's mail to not work properly. Use this at your own risk.
SPF
Sender Policy Framework (SPF) is a simple TXT record that goes in your DNS records for the domain you want to have email authentication for. This is the most basic method of authentication. The SPF record tells what IPs, domains, or MX servers are allowed to send mail for your domain. When your friend receives an email from a scammer claiming to be you, their email service will check your domain's TXT record and verify that the source of the email is from an approved MX, domain, or IP. If the SPF check fails, the email software will act according to its rules for SPF failures, usually marking them as spam.
SPF Records are specific to your set up. Incorrect settings can cause your entire domain's email to be blocked. Do not just copy someone elses SPF record!
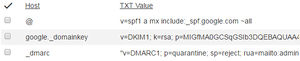
Example DNS SPF record for Google Apps for Work:
Host: @ Value: v=spf1 a mx include:_spf.google.com ~all
DKIM
DomainKeys Identified Mail (DKIM) is a two part authentication. First, the sender's email has to sign the email header with their private key. The receiver can then check the DNS records for your domain for the public key and decode the email header. This process is entirely automatic. DKIM requires the sender's email service to support it. DKIM is enabled first in your email settings, and then later in the DNS records where you post your public key.
Example DNS DKIM Record (still requires server to start signing)
Host: google._domainkey Value: v=DKIM1; k=rsa; p=(your long public domain key);
DMARC
DMARC (Domain-based Message Authentication, Reporting & Conformance) adds extra features for DKIM + SPF based email authentication. DMARC is the newest of the group, and is a simple DNS record you enter in your TXT records. DMARC tells email recipients what to do with mail that fails DKIM and SPF checks. DMARC also allows reporting for admins, if someone is spoofing your email (failing SPF and DKIM checks) you will be notified by the email in your DNS records.
Example TXT DNS DMARC Record
Host: _dmarc Value: v=DMARC1; p=reject; sp=reject; rua=mailto:YOU@YOU.COM; ruf=mailto:YOU@YOU.COM; rf=afrf; pct=100; ri=86400
Basically this says: if DKIM and SPF fail on my domain or my subdomains then reject them, notify me at this email, check 100% of mail from my domain, and send me reports every day.